Over the next few weeks, we’ll be diving deep into the ever-evolving, increasingly-dire state of data protection and security, and how organizations can harness the NIST CyberSecurity Framework to chart a successful path forward.
“It does not do to leave a live dragon out of your calculations, if you live near him,” writes J.R.R. Tolkien inThe Hobbit. What, exactly, makes a calculation sufficiently dragon-proof? We’ll get there, rest assured. First, let’s agree on this: There is a dragon, and he’s moved in next door.
For those unfamiliar with Smaug, the arrogant, cunning, wealth-hoarding dragon of The Hobbit, or the existential threat he presents to the book’s protagonist, Bilbo Baggins, here’s all you need to know: The dragons of Middle Earth are mean and greedy, greedy and mean. They love gold, and take it with impunity. In my estimation, this is the perfect analogy for our current data protection predicament, where data is akin to gold and instead of one fire-breathing menace intent on stealing it, there are many.
Either way, it simply does not do to be unprepared.
A Mountain of Gold
From 2010 to 2020, the total amount of data created, captured, copied, and consumed globally increased by more than 62 zettabytes, according to Statista. Over the next half a decade, that number is expected to triple. This is particularly important because as the volume of data increases worldwide, so does its value. Just think of all the valuable information that now lives in virtualized environments: Medical records, financial statements, confidential employee information, classified government documents, photos of family pets, and so on.
Another way to frame this would be: The more data we have, the more we have to lose. Today, the pain associated with losing data — because of human error, hardware failure, natural disaster, or theft — is almost ubiquitous. Even my 85-year-old grandparents (generally) understand the importance of backing up their photos to the cloud. While losing family photographs can be frustrating, even saddening, the financial, legal, and reputational ramifications associated with data loss can be catastrophic for businesses, governments, and other large organizations.
And so, at last, we’ve reached the razor-sharp nadir of our logical chain reaction. Unfortunately, as the volume and value of our data continues to grow, so will attempts to steal and/or compromise it. Those who pay attention to recent headlines already know this to be true. Enter, the dragon(s).
Houston, We Have a Dragon
In May of 2021, Colonial Pipeline Co, which operates the 5,500-mile network of pipes responsible for roughly 45 percent of the gasoline and diesel fuel consumed on the U.S. East Coast, was forced to close following a ransomware attack. It took five days for the company to begin restarting operations and, even then, fully restoring the flow of fuel was not immediate.
The attack’s impact was felt nationwide, with frenzied runs on fuel resulting in long lines and shortages up and down the East Coast, surging gas prices, and volatility across the energy market. It even prompted an emergency response from the Biden Administration, which addressed the growing threat of ransomware by name.
This, of course, is but one high-profile example in what is now a worldwide crisis. In the wake of the COVID-19 pandemic, especially, organizations have experienced an acute struggle to maintain security and business continuity. Between 2019 and 2021, the number of ransomware complaints reported to the FBI increased by 82 percent. Now with millions more people working from home, the risk of cyber threats and system breaches has grown exponentially, and is continuing to rise.
According to Cybersecurity Ventures, ransomware attacks alone are expected to impact a business, consumer, or device every two seconds by 2031, up from every 11 seconds in 2021. Over that same time frame, the total global cost of ransomware is projected to increase from $20 billion to a staggering $265 billion.
All totaled, the global cost of cybercrime is forecasted to grow by 15 percent year over year, according to Cybersecurity Ventures. By 2025, the damages are predicted to reach $15 trillion annually, up from $3 trillion in 2015. That would represent the greatest transfer of economic wealth in human history — exponentially larger than costs associated with natural disasters and more profitable than the global sale of all major illegal drugs combined.
Now that’s what I’d call a dragon-sized problem, one we’d be foolish to leave out of our calculations.
Dragon-Proofing with the NIST CyberSecurity Framework
There’s something to be said for having a plan — a great many things, in fact.
From Confucius to Benjamin Franklin to Tolkien to today’s Tik Tok influencer du jour, human beings have long recognized (and touted) the virtue of preparation. And while we have no shortage of pithy reminders to plaster on posters, embroider on throw pillows, or wedge into blog posts (wink, wink), finding the rightt way to prepare for life’s many dragons is easier said than done.
When it comes to data security and protection planning, specifically, there are but a few accepted, cohesive frameworks. The one we will be discussing here — and in future posts (stay tuned) — was crafted and introduced by the National Institute of Standards and Technology (NIST). This voluntary framework consists of standards, guidelines, and best practices designed to help organizations of any size and sector improve the cybersecurity, risk management, and resilience of their systems. Critical calculations for nearby dragons, as Tolkien might say.
The origins of the NIST CyberSecurity Framework (CSF) can be traced back to February 2013, when President Barack Obama issued an executive order calling for the creation of a voluntary framework for cybersecurity and resiliency. On top of this executive order, Congress codified into law the “Cybersecurity Enhancement Act,” providing an additional layer of validity to the creation of such a framework. One year later, NIST published the “Framework for Improving Critical Infrastructure Cybersecurity.”
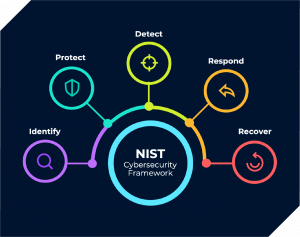 Originally intended for critical infrastructure, today it has broader applicability across all organization types. The NIST CSF has been increasingly recognized by governments and organizations as the recommended best practice guide to help improve the cybersecurity risk management and resilience of their systems. As of 2022, the NIST Cybersecurity Framework has been downloaded over 1.7 million times, and is currently being used by organizations across a wide range of sectors, sizes, and geographies.When boiled down, the NIST CSF consists five key functions: Identify, Protect, Detect, Respond, and Recover. According to NIST, these five functions were selected because they represent the five primary pillars for a successful and holistic cybersecurity program. They aid organizations in easily expressing their management of cybersecurity risk at a high level, enabling risk management decisions and acting as the backbone around which all other framework elements are organized.
Originally intended for critical infrastructure, today it has broader applicability across all organization types. The NIST CSF has been increasingly recognized by governments and organizations as the recommended best practice guide to help improve the cybersecurity risk management and resilience of their systems. As of 2022, the NIST Cybersecurity Framework has been downloaded over 1.7 million times, and is currently being used by organizations across a wide range of sectors, sizes, and geographies.When boiled down, the NIST CSF consists five key functions: Identify, Protect, Detect, Respond, and Recover. According to NIST, these five functions were selected because they represent the five primary pillars for a successful and holistic cybersecurity program. They aid organizations in easily expressing their management of cybersecurity risk at a high level, enabling risk management decisions and acting as the backbone around which all other framework elements are organized.
Here is a brief breakdown of each function, taken directly from the CSF overview on NIST.gov:
Identify:
The Identify Function assists in developing an organizational understanding for managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.
Protect:
The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.
Detect:
The Detect Function defines the appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables timely discovery of cybersecurity events.
Respond:
The Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.
Recover:
The Recover Function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident.
How Can the NIST CyberSecurity Framework Help Your Business?
Now for some exciting news: Over the next few weeks, 11:11 Systems will be getting a head start on CyberSecurity Awareness Month with a blog series on data security and the NIST CyberSecurity Framework.
Okay, I’m willing to admit that all this has been a rather roundabout way to arrive at our point (as well as yet another shameless shoehorning of Tolkien on my part), but I stand by it. Nevertheless, we’ll be diving deep into the ever-evolving, increasingly-dire state of data protection and security, and how organizations can harness the NIST CyberSecurity Framework to chart a well-planned, successful path forward.
Stay tuned for in-depth explorations into each of the NIST CSF’s five key functions from our seasoned team of product experts. Coming up first: Jim Jones, senior product infrastructure architect at 11:11 Systems, on “Identify.” Don’t miss out!





