Using traditional methods to migrate applications and data to the cloud is typically time-consuming because production servers may have to be brought to a standstill in order for the migration to be executed. You also have to keep in mind your storage footprint – the larger the storage footprint, the longer the migration process will take. In fact, large system migrations can typically take hours or days to complete.
The cloud has become increasingly popular as a platform to host business applications because it offers a very cost-effective and flexible IT platform for many organizations. But how do you get your existing applications and data into the cloud? That’s a question we are frequently asked here at iland.
One way is to migrate your data from a file server using traditional data copying tools but you need to ensure that users cannot change any data while the migration is taking place otherwise changes to files that have already been copied will be lost.
You may also need to create a plan for recreating the file shares, permissions, compression, encryption and other settings on the new storage. This can translate into further hours of downtime even if everything works as planned the first time—and much longer if it doesn’t.
At first glance it may seem daunting but don’t worry – there are simple ways you can overcome these challenges and perform data migrations without disrupting production applications and shutting down their servers.
Double-Take Move and Double-Take Availability are migration and data replication tools that allow you to migrate physical and virtual workloads with complete data protection. Leveraging Doubletake replication not only allows you to address the migration process for moving applications and data into the cloud. It also offers a way to automatically avoid or correct any migration errors that may occur.
Doubletake replication offers exceptional application and data protection/migration in virtual and cloud environments. Thanks to a single unified management console it is easier to use than ever before.
Six Reasons Why Double-Take Availability Provides Superior High Availability
- Simplicity – Set It and Forget It data protection includes advanced features that automate the initial setup and ongoing management of your availability environment.
- Plug and Play Protection – Double-Take’s pre-configured Universal Virtual Recovery Appliance for physical and virtual environments gives you a plug and play option for extending the protection of your virtualized environment.
- Real-time Replication – Offers you superior protection compared to snapshots because it ensures the uninterrupted availability of critical application systems and virtually eliminates the potential for data loss.
- Zero Downtime during Migrations – Replication technology allows users to remain active while Double-Take Availability is recreating the production environment on the new system.
- Platform Independence – Double Take Availability allows you to cost-effectively protect more of your environment.
- Simplified Management – A unified console makes it easier to implement, manage and extract value from a powerful High Availability environment.
The following steps detail how to configure the Doubletake replication/migration process:
Step 1
Doubletake Replication Process
Data Sync Tabs
Always select these settings when setting up a replication set:
- Start, Programs, Double-Take, Double-Take replication Console
- Double-click over SOURCE server and login with local admin accounts
- Right-click over SOURCE server and select, New, Replication Set from the menu
- Name the replication set “sourceservername_newservername-rep”
- Double-Click replication set and select files and folders stated in the Sync/move package
Right-click over replication set and select “Save”
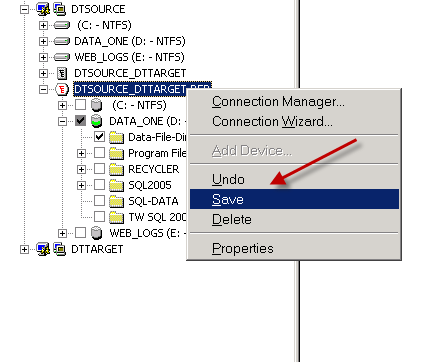
Step 2
Right-click over Replication Set and select “Connection Manager”
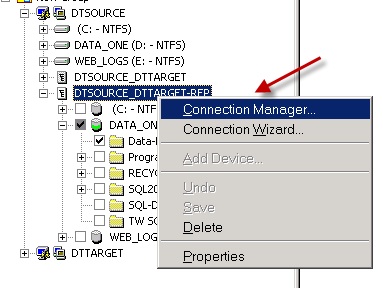
Step 3
Select the “Mirroring” tabs and make sure the following is selected
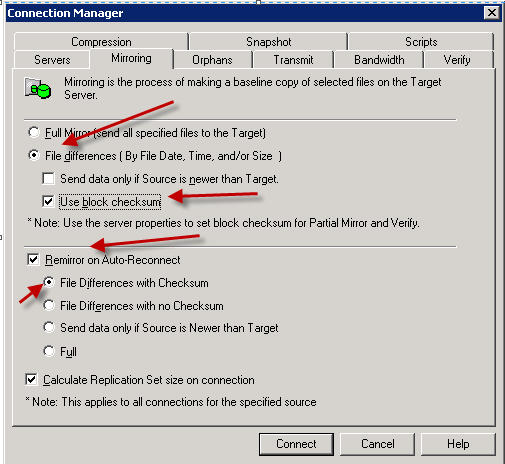
Step 4
- Click the “Servers” tab and select the target
- If a direct sync job do a one-to-one mapping
- If the move package/sync job states to copy to another directory, select and “All to One”
(NOTE: Start Mirror on connect and Start replication on connection are marked off by default)
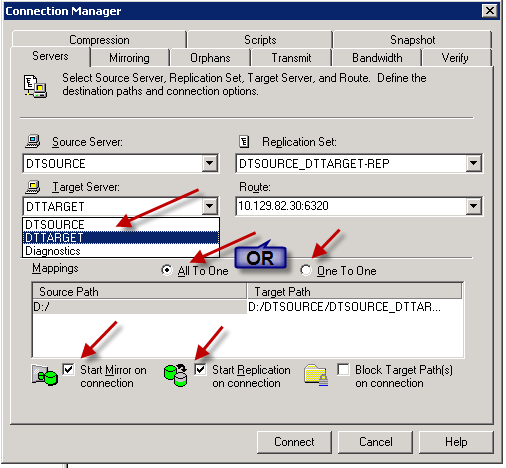
Step 5
- Select “Connect” and the replication job will start
- The job can be viewed from the SOURCE server
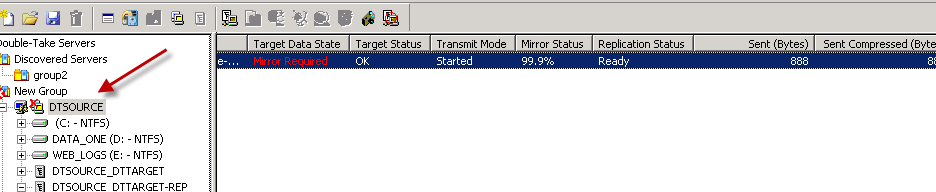
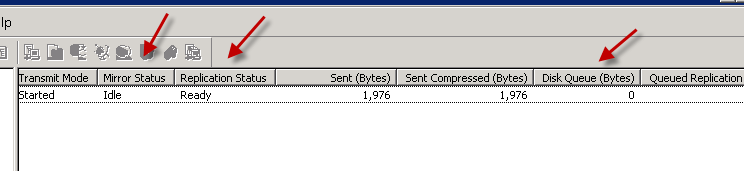
When job the Mirror status states “Idle”, the Disk Queue states “0” and the Replication Status reads “Ready” the job is complete
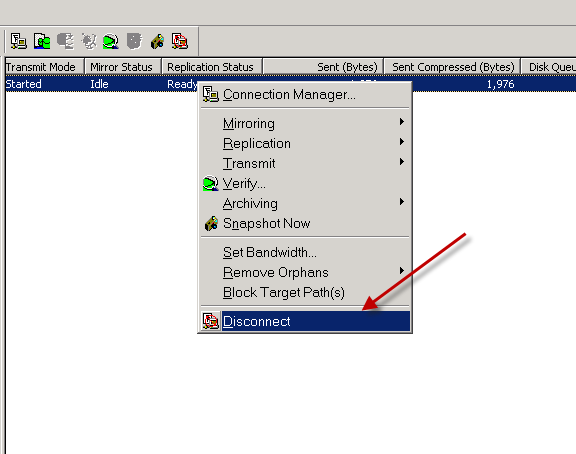
Disconnect the replication set to break the connection/ complete the job
Doubletake replication through the use of Double-Take Move and Double-Take Availability offers a simple and convenient means to migrate data and applications to the cloud.





