 Editor’s Note: As of January 2022, iland is now 11:11 Systems, a managed infrastructure solutions provider at the forefront of cloud, connectivity, and security. As a legacy iland.com blog post, this article likely contains information that is no longer relevant. For the most up-to-date product information and resources, or if you have further questions, please refer to the 11:11 Systems Success Center or contact us directly.
Editor’s Note: As of January 2022, iland is now 11:11 Systems, a managed infrastructure solutions provider at the forefront of cloud, connectivity, and security. As a legacy iland.com blog post, this article likely contains information that is no longer relevant. For the most up-to-date product information and resources, or if you have further questions, please refer to the 11:11 Systems Success Center or contact us directly.
Date: November 9, 2017
Author: 11:11 Systems
One of the main barriers to the adoption of public clouds over the past few years has been security. Fears of hacking and data theft have been heightened by cases in the media.
Many customers thought that cloud would automatically take care of security regarding attacks from the internet, and there have been great advances to allay these fears. However, for many public cloud providers not all bases are covered out of the box, and adding in security features can add significant cost and complexity to the solution.
Here at 11:11 Systems, we have provided many of the security features that an enterprise customer requires, and have been accustomed to within their own on-premises environments. This includes:
- Comprehensive firewalling capabilities at the edge
- Best-of-breed security within the cloud environment (anti-virus/anti-malware, intrusion detection, web reputation, file integrity monitoring, log inspection)
- Encryption at the datastore level along with optional VM encryption
All the functionality of the VMware NSX Edge virtual appliance has been integrated into the 11:11 Cloud Console, and for most customers this provides all of the functionality they need.
However, some customers prefer to use the same firewall technology that they have been using on-premises in the form of a physical or virtual firewall appliance. Also, the appliance may provide different or additional functionality.
One of the differentiators of 11:11 is being able to offer the capability for both physical and virtual appliances. While not very cloudy in nature, physical appliances can be accommodated by co-location, and 11:11 will take care of the cross-connection into the 11:11 cloud environment.
Our standard offering is to use the VMware NSX Edge virtual appliance, but other options exist and will be discussed later.
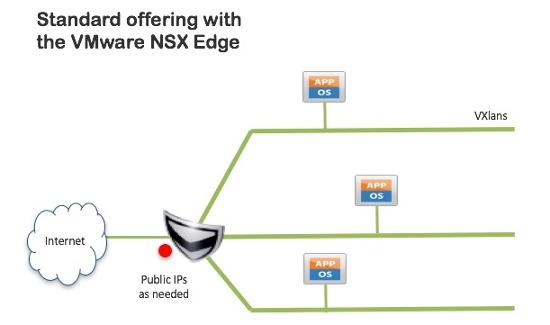
- Supports up to nine VXLAN-backed networks attached to the Edge
- Uses standard RFC1918 address structures for networks
- Route between networks and Internet using the Edge
- Provides:
- DNAT, SNAT, and 5-tuple Firewall
- SSL Client VPN and IPsec Site-to-Site VPN
- Simple Load Balancing (IP hash, round robin)
This standard architecture can be augmented by adding in third party virtual firewall appliances, as shown below. The firewall appliance runs like any other virtual machine in the cloud. Examples of third party firewalls used recently include:
- Cisco
- Kemp
- Checkpoint
- Watchguard
- Palo Alto
- Fortinet
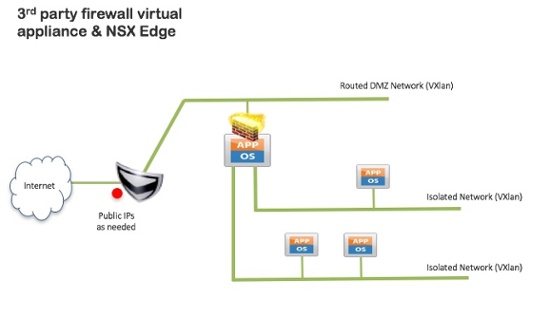
Third party firewall basics:
- Deployed within vCloud as a normal VM/vApp
- Will support up to nine VXLAN-backed internal networks
- vShield Edge configured mostly in a passthrough mode
- Customer manages third party firewall to provide required services
- Requires NATing from vShield Edge to third party firewall. This can result in double-NATing to applications, and IPsec VPNs from the third party firewall will dislike being NATed
Due to the NAT issues discussed above, 11:11 Systems normally prefers to adopt the next option, where the virtual appliance is attached directly to the internet via a block of public IP addresses in a small subnet.
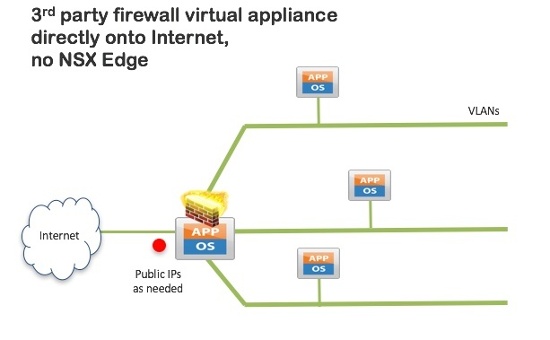
For this use case:
- VLAN-backed networks attached to the third party firewall appliance, with one external to the Internet. Can support VLAN trunking.
- Public IP address block as required (/28 for example)
- Use standard RFC1918 address structures for networks
- Route between networks and Internet using third party firewall
- Functionality determined by third party CLI or web UI
- No integration with 11:11 console for firewall functionality
- Appears as a VM to manage in the 11:11 console
Finally, as discussed earlier, 11:11 can offer co-location of physical networking appliances:
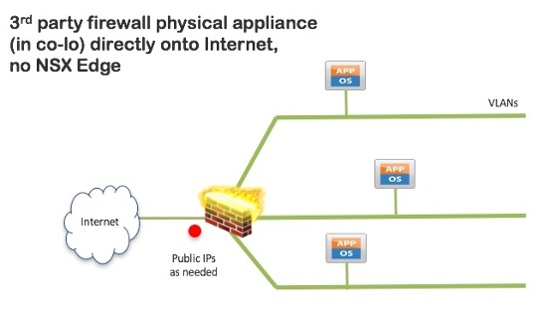
This last option is similar to the virtual appliance example. Here are a few of the basics features:
- Can support many VLAN-backed attached to the third party firewall (not limited by VM constraints)
- Use standard RFC1918 address structures for networks
- Route between networks and internet using third party firewall
- Functionality determined by third party CLI or Web UI
- No integration with the 11:11 console for firewall functionality
In all cases, these third party appliances can be integrated into management tools that the customer may already be running in the 11:11 cloud, or on-premises.
While 11:11 Systems supports a large range of virtual networking appliances and is not limited to firewalls (we also support load balancers, web application firewalls, WAN optimizers, etc), we do not resell licenses for these appliances (with the exception of the Cisco ASAv), and so customers will usually bring their own licenses, and can upload virtual appliances through OVF/OVA.





