In the time it takes you to finish this post — perhaps even this sentence — it is more than likely that ransomware will disrupt yet another business, causing extensive delays and irrevocable damage.
Across the globe, ransomware attacks continue to increase in frequency, sophistication, and consequence, littering headlines with cautionary tales and sobering statistics. Over the next decade, Cybersecurity Ventures predicts that global ransomware damage will grow by 30 percent annually. By 2031, damages are expected to surpass $265 billion per year, with a new attack occurring every two seconds. As cliché as this may sound: It’s no longer a matter of ‘if’ your cyber defenses will be tested, but ‘when.’
In the face of such threats, your best defense remains developing a clear ransomware recovery strategy — one that combines the right technology with a trusted, tested set of plans, processes, and procedures. For decades now, 11:11 Systems and Zerto have been on the front lines of this fight for data protection and recovery, partnering to deliver the technology and expertise needed to keep your organization up and running. Over the last few months, the 11:11 team has been updating our Zerto customers with information regarding their upgrade to Zerto 10. This upgrade is a two-step process that requires migrating from a Windows-based Zerto Virtual Manager (ZVM) to the new Linux-based Zerto Virtual Manager Appliance (ZVMA). Details for this are available in a success center article that provides some key considerations and prerequisites for upgrading.
Aside from the usual reasons to upgrade, Zerto 10 also comes with a critical new, built-in feature that is designed specifically for ransomware resilience: encryption detection!
What is Encryption Detection?
This advanced feature is built into Zerto’s platform and is designed to help identify and monitor suspicious encryption activities in your protected virtual machines (VMs). With the rise of encryption-based malware and other cyber threats, it’s crucial to have a system in place that can detect anomalous encryption behaviors in real time. Using Zerto’s Encryption Analyzer, this feature inspects the writes to protected VMs, watching for irregularities or spikes that may be indicative of encryption activity. When anything unusual is detected, an alert is triggered — giving you an opportunity to assess whether the irregular and suspicious activity is legitimate or malicious.
How does it work?
1. Real-Time Detection of Anomalous Encryption Activity
By constantly monitoring the VMs disk activity, this feature detects any irregularities that could suggest a security incident, such as malware encrypting files in the background.
The system assigns a “suspicion level” to each detection, based on the severity of the encryption anomaly:
- Level 1: Low suspicion — This could indicate a routine operation like a software update. At this level, two tagged checkpoints are created automatically.
- Level 2: High suspicion — This suggests a greater likelihood of potentially malicious activity and takes the following actions:
- Two tagged checkpoints are created automatically.
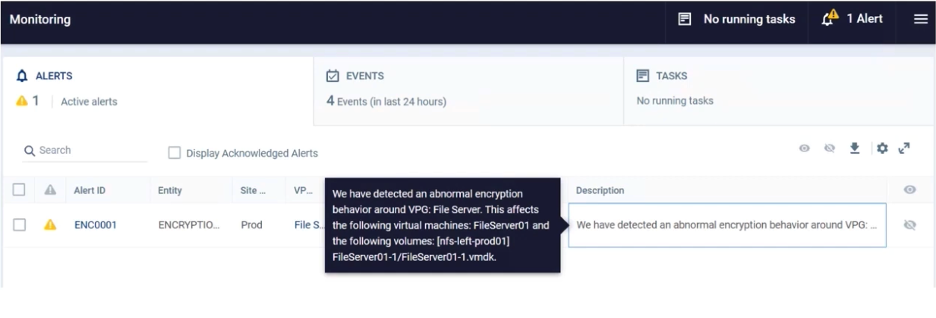
- An alert, ENC001, is triggered. This alert contains information about the volume(s), VM(s), and virtual protection group(s) (VPGs) that are affected.
- The status of the affected VPG(s) becomes “Warning: potential abnormal encryption was detected.”
Below is an example of what this looks like in the “Alerts” section of your ZVMA:
2. Automatic Tagging of Checkpoints
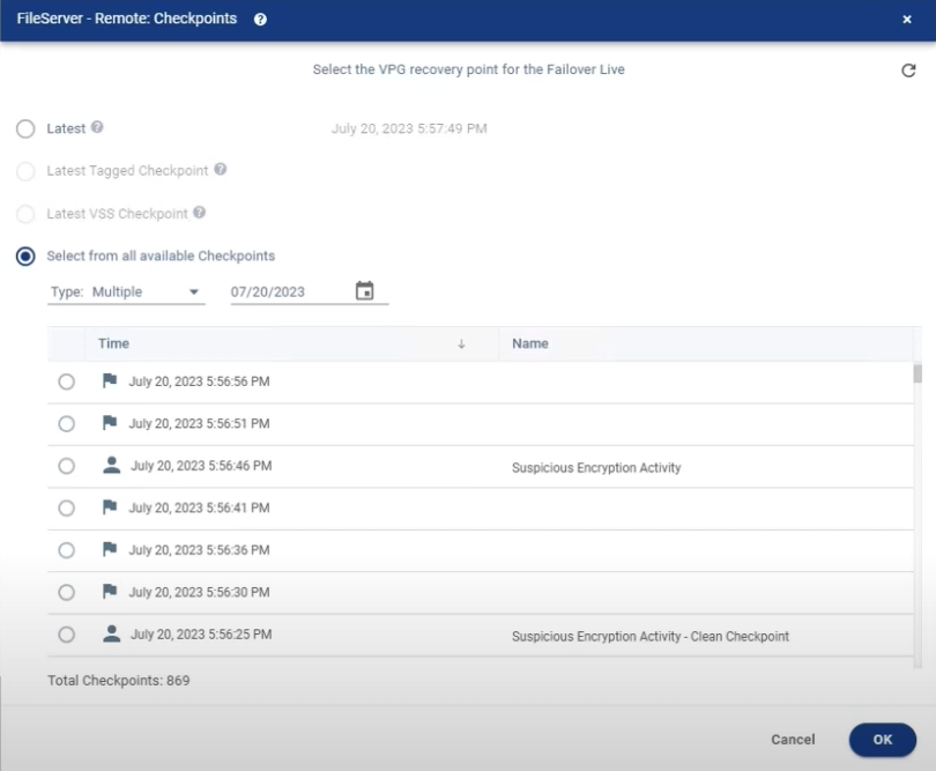
When encryption anomalies are detected, Zerto creates two important checkpoints:
- Suspicious Encryption Activity Checkpoint: This marks the exact point where suspicious activity was first identified, giving you a reference for when the potential issue was first detected by the system.
- Clean Checkpoint: This is created 10 minutes before the suspicious activity was detected, providing a safe restore point in case you need to roll back and mitigate any damage.
In the image below, you can see an example of what these automatically tagged checkpoints look like:
What Can I Do Next?
At this point, the next steps are up to you. The alerts themselves do not take any additional actions. However, these warnings can act as a catalyst for your team to investigate further. As noted above, suspicious activities could be expected due to things like maintenance activities so the notifications could be benign. The feature itself can be enabled and disabled in the user interface, but this is not recommended as that would disable detection for all protected VMs. Instead, it is recommended to dismiss the encryption detection alerts after reviewing the affected VMs.
When the impact is real, these alerts can help give a discreet time frame that your team can use to start investigating and potentially act on. Every organization will have different standards and processes for investigating and determining next steps, but the key benefit this feature provides is the ability to know precisely when a potential incident occurred from a disk-write perspective. This will help your team make an accurate assessment and determine the best course of action for your organization.
Zerto’s Encryption Detection can help you catch these incidents early on — before they escalate into full-blown data loss or business disruptions. This proactive detection can help you prevent or mitigate the impact of a ransomware attack, reducing the risk of data corruption or loss and making recovery more efficient.
Stay Ahead of Potential Threats
Zerto’s Encryption Detection feature is an invaluable tool for anyone looking to improve their organization’s data security. By providing real-time alerts, automatic checkpoint tagging, and extensibility options via available APIs, this feature helps you stay one step ahead of potential threats. Whether you’re defending against malware, monitoring encryption compliance, or simply improving the visibility of your environment, Encryption Detection makes it easier to spot and address abnormal encryption behaviors with confidence.
The team at 11:11 is looking for feedback on what you would like to see us do with this feature — we have a few ideas, but please do share your thoughts with us as we consider our next steps with regard to this feature too. Our product management team is eager to hear what our customers think of the feature and what they would like to see us do with it too.