Date: August 16, 2017
Author: 11:11 Systems
Editor’s Note: As of January 2022, iland is now 11:11 Systems, a managed infrastructure solutions provider at the forefront of cloud, connectivity, and security. As a legacy iland.com blog post, this article likely contains information that is no longer relevant. For the most up-to-date product information and resources, or if you have further questions, please refer to the 11:11 Systems Success Center or contact us directly.
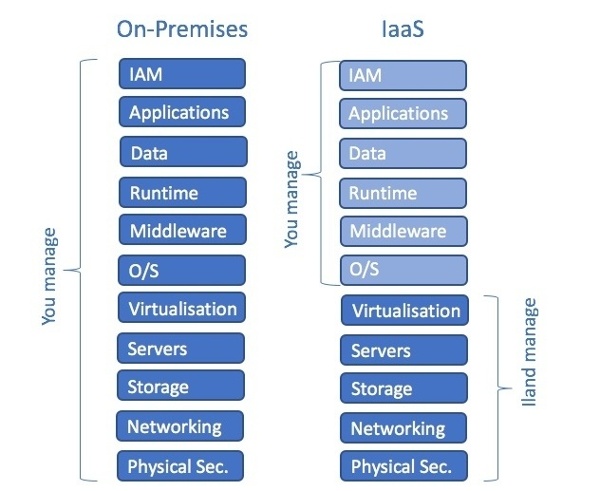
In the first part of this blog series, we looked at the cloud service provider side of the shared responsibility stack.
Looking at the rest of the stack, particularly the upper areas where the customer is responsible, it is extremely important to remember that there is no magic pixie dust in a cloud implementation when compared to an on-premises one.
It is vital that customers fully understand what they are getting from the cloud provider in terms of functionality, and, most crucially, what security and compliance features are provided. As part of this, customers need to fully understand what is included as part of a solution and what needs to be purchased separately. This helps prevent “bill creep,” where something looks inexpensive, but hidden costs build up rapidly.
Here are a few questions to ask when considering a cloud solution:
- Do we need to pay separately to license the operating system or other software, such as middleware and databases?
- Is anti-virus or anti-malware included? What vendor? What functionality?
- Are backups included? If so, what retention period? Are these in the same location, or another location?
- What edge firewalling or networking is provided? What functionality is provided?
- Can I add additional security controls through third party virtual appliances?
- What additional security solutions are available?
- What monitoring solutions are available to measure performance, availability, security, compliance, and usage?
Virtualization
The advent of virtualization and the addition of cloud management platforms, has made it extremely easy for customers in a cloud environment to self-provision virtual machines, storage and virtual networking.
Some cloud providers use instance or “t-shirt sizes” (small, medium, large) while other providers, such as 11:11 Systems, allow customers to provision VMs of any size and simply bill on the actual consumption of CPU and RAM by using resource pools. These VMs can be resized depending on requirements from week to week. Customers can add or remove CPU and RAM as required.
Similarly, customers are able to provision storage from different storage capabilities, be it disk, SSD or SSD/cache-accelerated.
From a virtual networking perspective, customers can self-provision networks based on VLANs or VXLANs, allowing them to securely share the underlying physical networks. In addition to the public internet, customers have the ability to take advantage of high-speed private networks using MPLS or leased lines to connect back to their on-premises environments.
When architecting a solution to run in the cloud, the same principles you would use on-premises still hold true. It is easy to create a DMZ and then internal networks, which may or may not have access to the Internet, and create firewall and routing rules between the various networks.
Typically, customers will be provided with an edge firewall or router which gives them access to the internet. A self-service interface will allow them to create firewall rules, as well as network address translation in both directions (SNAT and DNAT). Edge gateways can also be used for IPsec site-to-site VPNs, SSL Client VPNs, simple load balancing, etc.
For additional security, other virtual security appliances can be deployed to provide additional functionality. Examples could include: virtual firewalls (deep packet inspection), web application firewalls and complex load balancers.
Cloud Management Platform
While there’s not a box on the diagram listed above that discusses cloud management platforms (CMP), this is where the division between the customer and CSP really happens. Before cloud was a thing, many service providers offered virtualized solutions to customers, but typically, the virtualization was not designed to be multi-tenanted.
The advent of cloud management platforms, together with orchestration and automation solutions, has really enabled cloud services as we know them today — providing not just IaaS, but also PaaS and SaaS.
Multi-tenancy is the ability to carve up resources on a shared environment, with (importantly) networking and security services. This provides the economies of scale that cloud delivers, while also ensuring tenants cannot access each other’s services (unless specifically allowed to do so).
Operating System
When deploying virtual machines, cloud service providers will usually provide a catalog of the most recent operating system templates, be they Windows or Linux. It will be the responsibility of the customer to keep these operating systems patched and up to date.
Similarly, it will be up to the customer to determine what, if any, anti-virus or anti-malware solutions the CSP provides are included in the template, or as an optional extra. It is important to note that just being in the cloud does not remove the need for anti-virus solutions. Many CSPs provide these solutions at the hypervisor layer, so scans will not affect the performance of the VM.
Just as important as security software is the need for backups. Even if your CSP provides redundant storage, that is only there to protect against failure in the storage subsystems. It is not there to protect against data loss through accidental deletion, corruption or ransomware. So, check what backup solutions are available, what retention periods, how often they are taken, and where the data will be stored.
Aside from anti-virus/anti-malware, what other security solutions will your CSP provide, and what questions should you be asking about them?
- File integrity monitoring
- When were important files changed and by whom?
- Data loss protection (DLP)
- Have sensitive files or content been sent or copied elsewhere?
- Audit logs
- Who has been doing what within the operating system, middleware or applications?
- Encryption
- Are the virtual storage devices encrypted? Who holds the keys? What level of encryption is available?
- Penetration testing
- How can you test if your web applications are secure? Can you automatically produce remediation suggestions?
- Intrusion detection/prevention (IDS/IPS)
- What facilities are provided to detect or prevent hacking attacks?
- Web reputation
- How do you prevent users within the cloud environment from accessing malicious sites?
Middleware/Runtime/Application/Data
It will be the responsibility of the customer to manage and control all aspects of the middleware, runtime, application and data in an IaaS cloud environment.
As discussed earlier, it will be important to ensure the cloud environment is architected to provide the network security and data storage required by the application. As with all IT implementations, this needs to be sufficient for the business’s requirements.
As new data protection legislation comes in, such as GDPR, it will be important to classify the data being stored, and provide sufficient controls to protect the data from malicious access. For example, databases should be hosted on secure, back-end networks. Only the relevant protocols should be allowed access via the firewall, and it may be necessary to further lock down access by source IP address. Data may need to be encrypted. Only database administrators should be allowed access.
Identity and Access Management
As the name suggests, IAM covers two areas:
- Identity: Who is the user? How do we authenticate them — password, alternative challenge?
- Access: Once authenticated, what are they able to do?
In the case of a cloud management platform, it is important that users only have access to the functions that they need to carry out their job. When experimenting with cloud, it is very easy for new users to do everything from the outset as an administrator or even as the root user. This is not only dangerous but means that it is impossible to track and audit what has been going on. In some cloud environments, it is difficult to retrofit things once everything has been created as an administrator.
In on-premises environments, separation of duties was often mandatory due to the fact that people worked in different departments: compute, network, storage or Windows/Linux. With cloud management platforms, an administrator will usually have access to everything, and that could cause major problems, as have been highlighted in the media recently!
It is a great philosophy to adopt a “least privilege” approach, where a user’s access rights can be elevated for a short time, perhaps on a subset of the environment, in order for them to carry out a set of tasks, and then set back to their normal privilege levels.
In most cloud environments, fine-grained RBAC controls allow for tight management of who can do what, and audit logs clearly show what has been going on.
While there is much talk in the media of using secure and complex passwords, many cloud management platforms will also allow two factor authentication, perhaps involving a username/password as well as a second challenge, such as a code sent to your mobile phone, or a specialist token device such as an RSA key.
The11:11 Systems Philosophy
Having been in cloud infrastructure market for many years (and before it was called that), 11:11’s philosophy has always centered around providing an enterprise cloud experience.We are committed to providing all the enterprise features that customers running environments on-premises have grown to expect.
When working with 11:11 Systems for IaaS, customers can expect:
- Flexibile pricing
- Pay for consumption either on a pay-as-you-go basis with hourly billing, reserve capacity on a monthly basis, or have a mixture of the two (reservation + burst).
- No “t-shirt sizes.” Just provision as you would have on-premises, and change the sizes when you need to. Using resource pools, 11:11 bills on the actual consumption of CPU and RAM.
- Windows OS licensing is built into the base price using our Microsoft SPLA.
- Included backups
- Seven-day nightly backups at no extra cost.
- Self-service VM restoration through the 11:11 Cloud Console.
- Advanced security
- Trend Micro Deep Security is built-in for Windows and Linux VMs deployed from the 11:11 catalog, which can also be enabled for self-built or imported VMs.
- Tenable Nessus web monitoring is automatically enabled on all public IPs allocated to customers, at no extra costs. Detailed remediation reports are produced on all services exposed to the internet via the public IPs.
- All VMs benefit from encrypted storage using our Nimble flash-accelerated and all-flash arrays at no extra cost. Individual VM encryption is available at extra cost.
- Fully-featured cloud management console
- Full self-service functionality with detailed and granular role-based access control through an HMTL5 web console is also available as an Apple and Android app.
- API integration
- Tight API integration in the console with VMware vCloud Director and vSphere, backups, disaster recovery, business continuity, and performance reporting with a long history available through our big data repository.
- API access to all functionality, with support and documentation for several well-known SDKs, as well as presenting the native VMware vCloud Director API.
For more information, please visit 11:11 cloud hosting.




