
Date: October 24, 2017
Author: Pete Benoit
Editor’s Note: As of January 2022, iland is now 11:11 Systems, a managed infrastructure solutions provider at the forefront of cloud, connectivity, and security. As a legacy iland.com blog post, this article likely contains information that is no longer relevant. For the most up-to-date product information and resources, or if you have further questions, please refer to the 11:11 Systems Success Center or contact us directly.
How many online logins does the average person have? The easy answer is too many to secure.
In 2016, the average person had 27 unique online accounts with passwords to manage, according to an Intel Security survey. I couldn’t find similar numbers specifically for IT personnel but we can be safe in assuming that number is significantly higher.
A study from the National Institute of Standards and Technology (NIST) found that a majority of the typical computer users they interviewed experienced security fatigue which often leads users to risky computing behavior at work and in their personal lives.
The inevitable result is that users will choose the path of least resistance when creating, updating and securing login information. The results of a survey conducted by mobile identity company TeleSign found that a staggering 73% of online accounts are guarded by duplicate passwords.
To combat this problem security administrators are requiring longer and more complex password strings making it even less likely that users will create and track unique passwords over dozens of accounts. This is the foundational flaw of single-factor authentication, less stringent password requirements are easier to manage but easier to compromise while more stringent requirements are more secure but much more difficult to manage for the end user.
This brings us to the need for multi factor authentication which is generally described as using at least two of the following factors:
- What you know: login and password
- What you have: mobile or dedicated security device
- Who you are: biometrics
IT administrators understand that what humans (and databases) “know” is easily comprised of persistent effort and human error. Adding a second factor as the baseline requirement for access into the front door is becoming a standard for end-user access and even more so for system level and programmatic access.
The 11:11 Cloud Console includes the option to enable two-factor authentication (2FA) for console access for each user account, tightening security at the entry point of the customer’s DR or IaaS administrative environment. After entry, each user is assigned a granular set of permissions per level of access inside of the virtual datacenter. As an example, the 11:11 Cloud Console provides the option of accessing the administrative console of the virtual machines from inside of the 11:11 Cloud Console interface, effectively implementing 2FA access to each VM by way of the initial 2FA login procedure.
11:11 Systems strongly encourages its new and existing customers to implement 2FA for each active account, regardless of access level or absence of an explicit call for it in the organization’s compliance requirements. In our experience, implementing multi-factor access at a system level should be considered as essential to access management as requiring password length, complexity and change rules when creating new accounts.
Directions for enabling two-factor authentication in the console for an existing account are provided below. This feature is easy to implement and is provided at no additional cost.
Two-Factor Authentication
Download and install an authenticator app from your mobile phone’s App Store. It’s free.
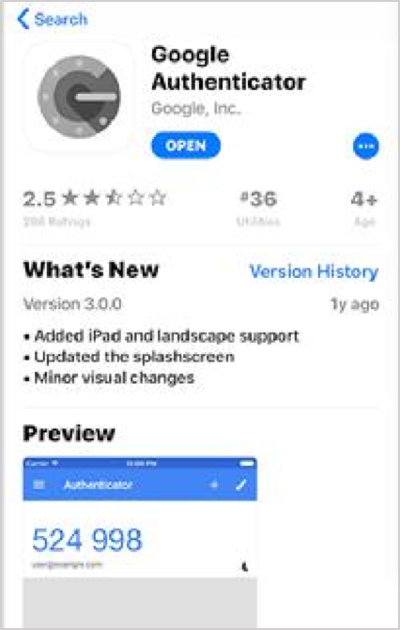
The authenticator enables a second level of password authentication for added security.
If you have not already done so, install either FreeOTP or Google Authenticator on your mobile device (smartphone).
See the list below for links to download and install the app on a mobile device.
Mobile Device App Download Links
FreeOTP Android
Free OTP iOS
Google Authenticator Android
Google Authenticator iOS
Enabling Authentication for Your Account
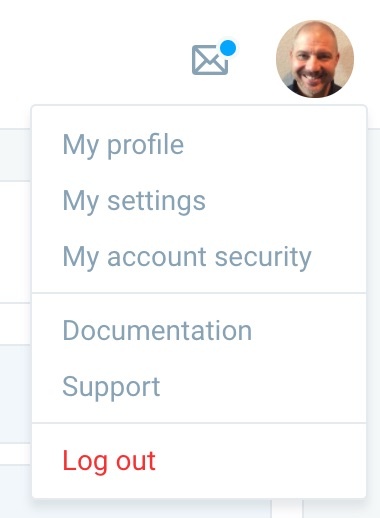
In the upper-right-hand corner of the dashboard page, click on the user account icon to open the settings menu. Then, select “My Account Security” from the drop-down.
Scroll down to the “Two Factor Authentication” widget near the top of the page.
Open the authentication app on your mobile device, and either scan the barcode on the computer screen or enter the text key to the right of the image.
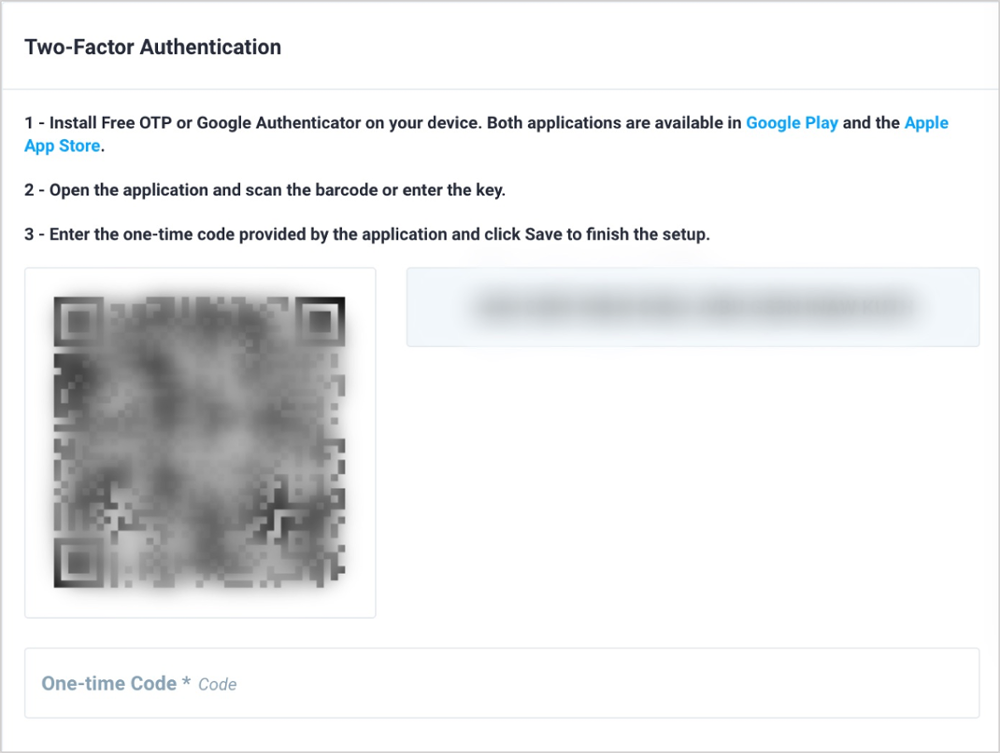
Enter the code that is generated by the app in the one-time code input box and click the green save button to complete the console implementation. The next time the user logs in, they will be prompted for the username and password then the current active six-digit number from the authenticator.
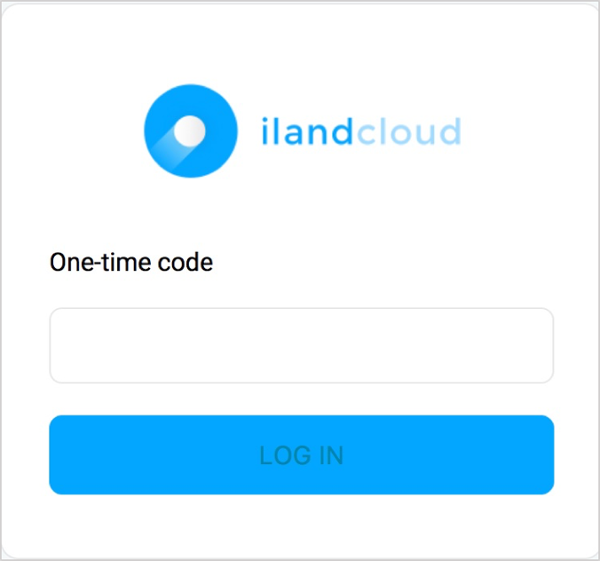
11:11 can’t stress enough the importance of adding a second factor of protection at the ingress point of the cloud console. The security feature is built into the console and takes minutes to add for a new or existing user account. Taking this step assures that user access policies set inside of the console will have begun over an encrypted connection with multi-factor authentication of the login attempt. Additionally, completion of this step in the access security process meets the basic standards for most major IT compliance requirements.





