As of January 2022, iland is now 11:11 Systems, a managed infrastructure solutions provider at the forefront of cloud, connectivity, and security. As a legacy iland.com blog post, this article likely contains information that is no longer relevant. For the most up-to-date product information and resources, or if you have further questions, please refer to the 11:11 Systems Success Center or contact us directly.
For years, cybersecurity was a niche skill that most IT professionals were comfortable ignoring. If customers wanted to know more about a given security capability with a software or service offering, most of us would have gone directly to our security and compliance specialist for the answer, or more likely, made an introduction directly to the customer. At the time, security wasn’t the headline or the differentiator. It was an afterthought on the “digital transformation” journey.
That was then. Today, it’s clear that times have changed. If you are an IT developer, buyer, or someone who can be impacted by cybercrime (which is basically all of us), having a cursory understanding of data security is now a requisite part of the job. Otherwise, you could be putting yourself or your company at risk. To illustrate this changed environment, just look at the last year:
-
According to Risk Based Security: “There have been 3,813 breaches reported through June 30, exposing over 4.1 billion records. Compared to the midyear of 2018, the number of reported breaches was up 54 percent and the number of exposed records was up 52 percent. Already in 2019, three breaches have made the list for the 10 largest breaches of all time.”
-
According to Cybersecurity Ventures: “Cybercrime is the greatest threat to every company in the world, and one of the biggest problems with mankind. Cybercrime will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015. This represents the greatest transfer of economic wealth in history, risks the incentives for innovation and investment, and will be more profitable than the global trade of all major illegal drugs combined.”
Cybercrime bad news – and good news
Indeed, 2019 was a year for the cybercrime record books. The above has translated into a lot of bad news and difficult conversations between customers and IT professionals.
Now, for the good news. As you read this, our cybersecurity capabilities continue to improve. Cybercrime is getting more attention than ever (the first step in resolving a problem is to admit it exists), organizations are getting smarter (security spending is on the rise), and cybersecurity strategies are getting more advanced and focused.
However, it’s fair to say that as we get better at defense, cybercriminals are also getting better at offense. It’s for this reason that many customers are evolving from a tactical security strategy (technology and service-based approach) to a Zero Trust approach that incorporates technology, services, people, and processes, into a cohesive approach that includes multiple layers of defense.
The greatest security vulnerability in IT? Trust.
To understand the need for Zero Trust, consider that today many of us have been conditioned to view internal networks (accessed via password) as safe and external networks as potentially harmful. We assume this through a “trust and verify” approach that says once your identity and permission to access the internal network are verified, trust is considered established. Oftentimes, this means automatic access to other systems inside the secure perimeter. Unfortunately, it’s also when we let our guard down and a motion that bad actors rely on to strike and exploit IT vulnerabilities.
Because of this risk, smart organizations are now replacing Trust and Verify with Zero Trust. Zero Trust changes our assumptions that employees, systems, and services operating from within the secure environment can automatically be trusted. Instead, Zero Trust verifies anyone (or anything) that attempts to connect to any system before granting access. To put it in the context of a common analogy, if you enter your house through the front door, you expect to have access to all the rooms inside. In a Zero Trust world, you would not necessarily have access to all rooms automatically. In fact, you may not be able to go beyond your entryway without further permission.
This year alone there have been countless examples of malicious insiders taking advantage of valid credentials and doing great damage from within companies. Add the absolutely huge risk associated with external security threats (ransomware, malware, etc) that seems to grow daily, and you can see why customers are pursuing Zero Trust strategies in their IT organizations.
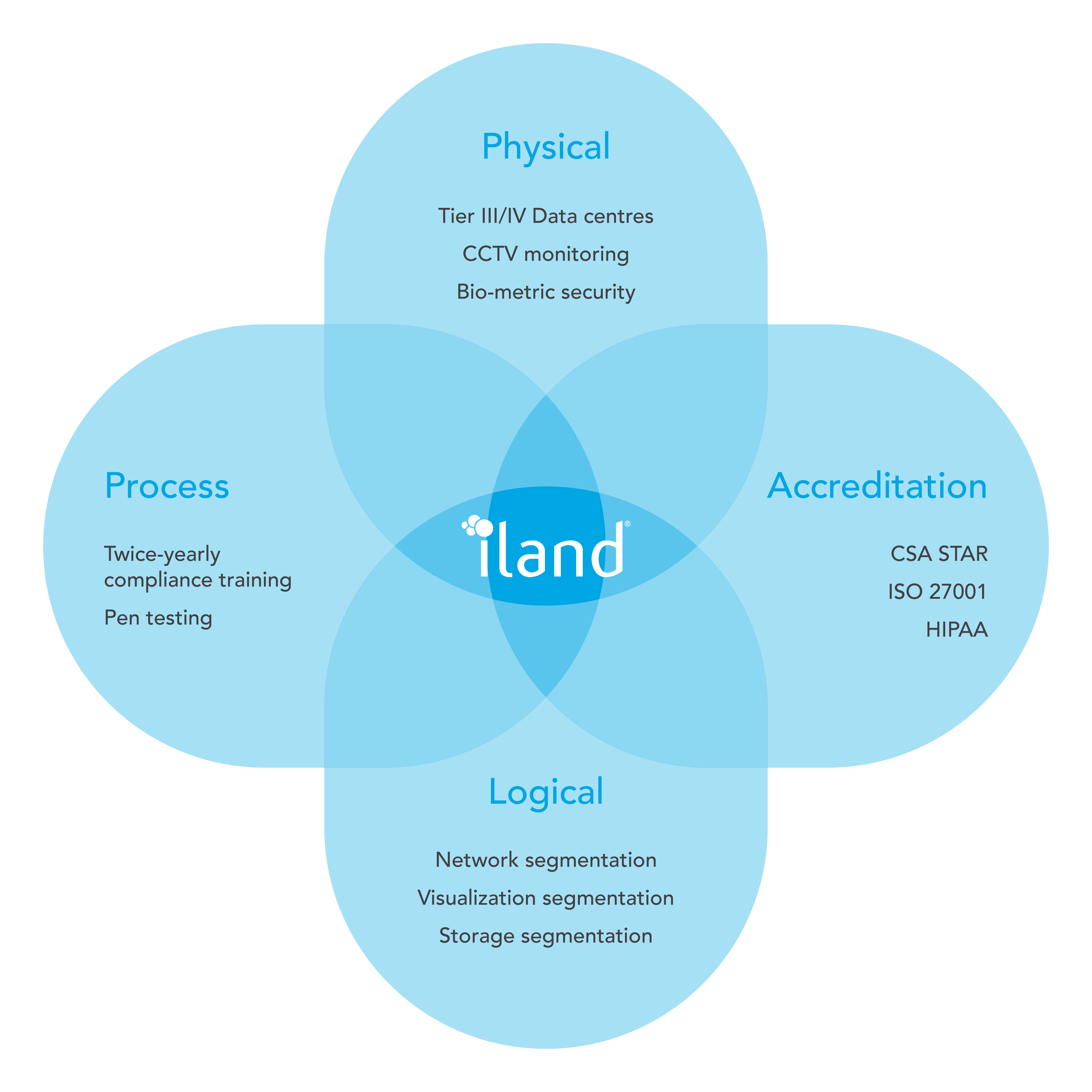
11:11 Systems recently had the opportunity to host a webinar on Zero Trust with our partner, and security-industry leader, Trend Micro. You can replay the webinar here. If you would prefer to read through 11:11’s approach to Zero Trust, we have a new white paper available here.
In both cases, you will learn how a Zero Trust strategy in your organization can eliminate many of the vulnerabilities that are left behind by technology implementations alone. As we wind down 2019 we focus on what 2020 will bring, it’s important to acknowledge that cybercrime is growing in numbers, impact, and sophistication. That doesn’t mean we are helpless, but it does mean we need to change. A Zero Trust strategy can help with that.






